Energy cybersecurity: The need for effective resilience
Despite repeated warnings of a “digital Pearl Harbor,” advanced economies such as the United States and the European Union are more exposed to cyberattacks than ever. These vulnerabilities can be traced to the spread of new digital technologies, the electrification of transport and heating systems, robotics and artificial intelligence.

In a nutshell
- New digital technologies make advanced economies more vulnerable to cyberattack
- The risks are especially high for critical infrastructures and their control systems
- Layered defense in depth and faster recovery times are key to limiting damage
While warnings of a “digital Pearl Harbor” in the form of cyberattacks are nothing new, advanced economies such as the United States, the European Union and Japan may be more exposed than ever. Over the past decade there has been a worldwide push to build political and public awareness of emerging cyber threats, and to bolster the defenses of public institutions and industries. Yet resilience has not sufficiently improved.
In 2016, the cost to businesses of cyberattacks was estimated at about $450 billion. According to a 2017 threat assessment of internet organized crime by the EU’s law enforcement agency, Europol, the global impact and spread of cyberattacks over the past year has been unprecedented, and the international response has been insufficient. A single, extremely disruptive cyberattack has the potential to cause up to $120 billion in economic damage, which would make it more destructive than natural disasters such as Hurricane Sandy in 2012, according to calculations by the insurer Lloyd’s of London.
The security of industrial control systems that govern the critical infrastructure advanced economies depend upon is still dangerously lax, critics allege. Business models and daily lives are being revolutionized by the digitalization of the energy sector and other industries, and by the spread of the Internet of Things (IoT). But this process is also making the global economy even more vulnerable to devastating cyberattacks and their consequences.
A hacker group attacked energy companies in the U.S., Europe and Turkey, penetrating their operational systems.
Last September, the international cybersecurity company Symantec revealed that a group of hackers – variously known as “Dragonfly,” “Energetic Bear” or “Berserk Bear” – had attacked major energy companies in the U.S., Europe and Turkey and penetrated their operational systems. The hacker group, which is believed to have Russian links, first came to notice in 2014 and appears to specialize in attacks on power utilities. In 2015-2016, over a span of only 18 months, it compromised the systems of more than 1,000 companies and organizations in 84 countries.
Its latest hacking campaign, called “Dragonfly 2.0,” has been monitored since late 2015. To date, it has not caused power outages like those triggered by Russian hacks on Ukraine’s electricity grid in December 2015 (Ivano-Frankivsk) and December 2016 (primarily in Kiev). But in more than 20 cases, the intruders successfully gained access to companies’ internal networks. Symantec evaluated the recent attacks as “potentially politically motivated” and warned that a cyberattack on a small energy company could threaten the entire power grid.
In July 2017, the U.S. Department of Homeland Security and the Federal Bureau of Investigation (FBI) revealed that the American power industry, including nuclear generators, had been targeted by Russian hackers interested in gaining access to the control systems. Fortunately, only administrative and business networks were affected. In contrast to other power generators, nuclear plants are often much better protected from outside intruders, as their computerized operating systems are completely separated from the corporate network and their control functions are isolated from the open internet.
In June 2017, power utilities, gas stations, the international airport, mass transit system and banks in Kiev were targeted again by the “NotPetya” wiper (a class of malware designed to wipe all data from infected hard drives). Ukraine’s Interior Ministry called it the biggest cyberattack in the country’s history. Ukraine, NATO, the EU and other cybersecurity experts concluded that a state actor was behind the attack. For them, Ukraine had become the world’s hottest battleground and testing site for future cyberattacks and global trends. From Ukraine, “NotPetya” spread to 64 countries and inflicted more than $600 million in losses on companies worldwide. But no country has suffered on a scale comparable to Ukraine.
Digitalizing energy
The accelerating processes of digitalization and electrification, which cut across many industries, has spurred competition within the energy business and attracted new players from outside (for example, information technology companies). Even big oil and gas companies, such as the oil service provider Halliburton, have entered strategic alliances with IT giants such as Microsoft.
Oil and gas companies already operate some of the world’s most powerful supercomputers. Now cloud computing services offer new applications and a much cheaper way of analyzing increasingly complex seismic, drilling and production data. Chevron, for example, estimates that the data it handles doubles every 12-18 months, yet only about 5 percent of this information is utilized. Digitalization and automation promise to change this, making future exploration and drilling for oil and gas cheaper, more efficient, environmentally cleaner and safer.
Facts & figures
Figure 1: Countries best prepared for cyberattacks
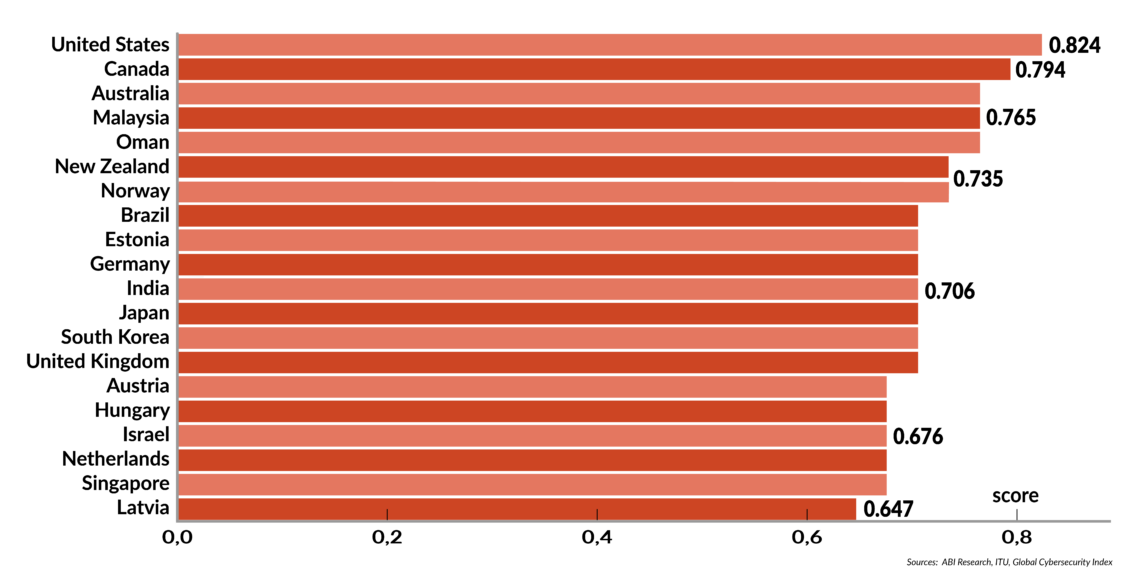
But the advantages gained by mobile connectivity and digital transformation also create new security vulnerabilities. Protecting against disruptive cyberattacks requires the deployment of equally advanced information technologies.
Even more dramatic are the fast-paced changes taking place in the power sector. National grids are becoming much more decentralized and interconnected with local “mini-grids.” Together with the expansion of renewable energy sources and new storage options, these developments have completely disrupted the power industry’s traditional business model. Even the fundamentals are being questioned. The whole sector is being forced to adapt to these radical changes or face the likelihood of going under in fundamentally altered future markets. While digitalization is widely considered to be above all a technological revolution, its larger impact on companies and governments will be seen in markets, business models, modes of organization and company cultures.
Prevalence of insecure technologies
About 70 percent of global energy companies suffered a breach of their IT systems in 2016. Many still rely on outdated, insecure operating systems and even hardware. Most cybersecurity companies and experts agree that the global threat landscape is evolving at an accelerating pace, with cyberattacks growing in sophistication, destructiveness and their ability to elude complex security systems.
Meanwhile, companies and organizations must deal increasingly with financial and personnel constraints. There is a growing skills shortage, illustrated by a forecast that more than 3.5 million cybersecurity positions worldwide will go unfilled by 2021. Instead of investing prudently in their own cyber defense and internal recovery procedures, many companies choose to treat the threat of ransomware as a straightforward financial issue. For them, it appears cheaper to pay the ransom to get their encrypted or stolen data back.
A shortsighted security culture makes future copycat attacks just a matter of time.
This shortsighted security culture, combined with the success of the WannaCry ransomware in May 2017, makes future copycat attacks with an even more destructive impact just a matter of time.
Positive scenario
While new technologies create new cybersecurity risks and vulnerabilities, technologies such as blockchain and artificial intelligence can also help protect critical infrastructures, especially energy systems. This can be encouraged through government regulation, including a proposed EU certification procedure and “security by design.”
Such efforts have already borne fruit. In Germany, for example, the introduction of smart meters has been repeatedly delayed to remedy security vulnerabilities and to make sure they conform to newly adopted government standards. Last October, Siemens had to release another firmware update for a new smart meter to prevent remote attackers from bypassing authentication and performing administrative actions on the device.
Improving awareness and transparency have been accompanied by the introduction of more efficient resilience concepts. Political and economic leaders have realized that sophisticated cyberattacks cannot be fully prevented and that the best protection is offered by a layered defense in depth. To make critical infrastructures and their control systems sufficiently resilient, defensive measures need to be based on successive physical, organizational, electronic and cryptographic barriers, layered one on top of the other.
Facts & figures
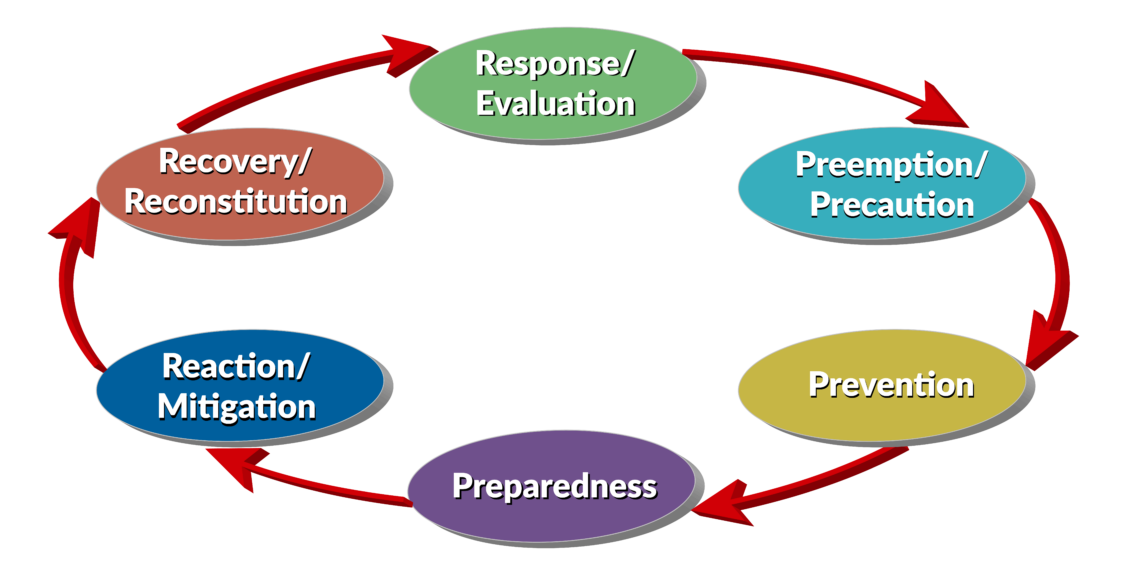
The P’s and R’s of defense in depth
- Preemption/Precaution: Mitigation of organizational and technical deficits
- Prevention: Improved/hardened protection of supervisory control and data acquisition (SCADA) systems; de-linking SCADA systems from the open internet
- Preparedness: Includes training, readiness, exercises and simulation
- Reaction/Mitigation: Technical countermeasures, handling the media
- Recovery/Reconstitution: Bringing SCADA and operating systems back online
- Response: Hacking back, continual evaluation of lessons learned
The positive scenario assumes that governments and companies take steps to ensure that all critical infrastructures have access to stable power supplies for at least 24 hours in case of an emergency. This involves safeguarding critical assets (such as industrial control systems), proactively dealing with physical and cyber threats, and assessing how to best mitigate other risks. Effective planning depends on a comprehensive understanding of all vulnerabilities and risks, including preparing for a worst case of disrupted output and distribution.
Facts & figures
Figure 2: Layered in-depth cyber defense
Realistic scenario: Getting worse
Even in the most optimistic reading of cybersecurity trends, the introduction of blockchain and other resilience-enhancing technologies will not provide silver bullet solutions. Even with increased awareness from Western governments and the public, along with the introduction of more effective resilience measures, the next few years may be dominated by increasingly capable cyberattacks by state-supported hacker groups and international criminals. Six reasons may be cited:
First, the spread of new technologies tends to multiply existing cybersecurity risks and vulnerabilities faster than countermeasures can be devised. Partly, this is due to burgeoning market for billions of smart sensor-enabled IoT devices that communicate and cooperate with each other. Their rapid and often premature adoption has already created uncountable loopholes and data breaches.
Second, the billions of IoT devices that will soon be flooding the market have often been designed with no thought to safety or security. There is no recognized international standard for cybersecurity, just rudimentary requirements for individual countries. Yet these products are exported and sold worldwide. They must also compete on price in an increasingly “commodified” consumer electronics market, where customers are unwilling to pay more for higher security standards.
Third is the use of increasingly interconnected industrial control systems. Fixing flaws in sensors and devices by updating software or by other means is not always a simple matter, as engineers often need years for redesign. Until now, replacing the architecture of control systems, including the introduction of segmented networks, could take as long as 25-35 years. This task is further complicated by the conflicting approaches, backgrounds and objectives of IT and engineering professionals. Usually, changes to critical infrastructure occur on a piecemeal basis, rather than holistically, resulting in the deployment of isolated, one-off security solutions.
Fourth, government regulatory frameworks can take almost as long to define and change. Even when new regulations are implemented, they are often rendered obsolete by the speed of technological innovation. In many cases, they prove impractical or undermine business efficiency and markets.
Fifth, the worldwide expansion of renewables, along with smart grids and smart metering, is also creating new cybersecurity vulnerabilities. These include internet-connected inverters of solar panels and fresh flaws discovered at wind farms.
Finally, energy companies will be particularly exposed to targeted cyberattacks. Unlike most corporates, they will not just have to cope with cybercriminals, whose ever-expanding activities account for most threats emanating from the dark web. Utilities will also have to fight off much more sophisticated strikes at deliberately selected industrial control systems, with the aim of causing major disruptions of service.
Given this threat environment, companies and organizations will need to focus even more on their ability to rapidly restore output and service after cyberattacks. This includes constant training of all employees – not just IT and security staffs – along with awareness building among customers.
Effective resilience strategies start with making security a business priority for top management. The entire security architecture of an organization must be subject to critical review with an eye to new, disruptive technologies and changing business models. Hitherto, corporations have given cybersecurity investments a relatively low priority because they were considered too costly or an unjustified liability. Now, they should be regarded as a cornerstone of future competitiveness.






